GoogleCTF: Vienna-Chemical-Plant (rev)
This is the GoogleCTF: Beginners’ Quest writeup/walkthrough. “Vienna-Chemical Plant” is the name of the first task.
Challenge Link ➡ Vienna-Chemical-Plant
Brief
“You must wonder why we have summoned you, AGENT? It has come to our attention that something terrible is about to take place. There is still time to prevent the disaster, and we could not think of anyone more suited for this task than you. We believe that if you can’t solve this quest, neither can anybody else. You have to travel to Vienna, and investigate a suspicious chemical plant. This mission must be executed in secrecy. It’s classified, and it regards the safety of the whole world, therefore we can’t tell you anything more just yet. Go now, you have the fate of the world in your hands.”
Challenge: CCTV (rev) You arrive at your destination. The weather isn’t great, so you figure there’s no reason to stay outside and you make your way to one of the buildings. No one bothered you so far, so you decide to play it bold - you make yourself a cup of coffee in the social area like you totally belong here and proceed to find an empty room with a desk and a chair. You pull out our laptop, hook it up to the ethernet socket in the wall, and quickly find an internal CCTV panel - that’s a way better way to look around unnoticed. Only problem is… it wants a password.
Overview:
You’re at a chemical plant, and you’ve got the facility’s Ethernet wire plugged into your laptop. You come upon a CCTV web page, but you need to get around a login page in order to view CCTV cameras.
Login Page
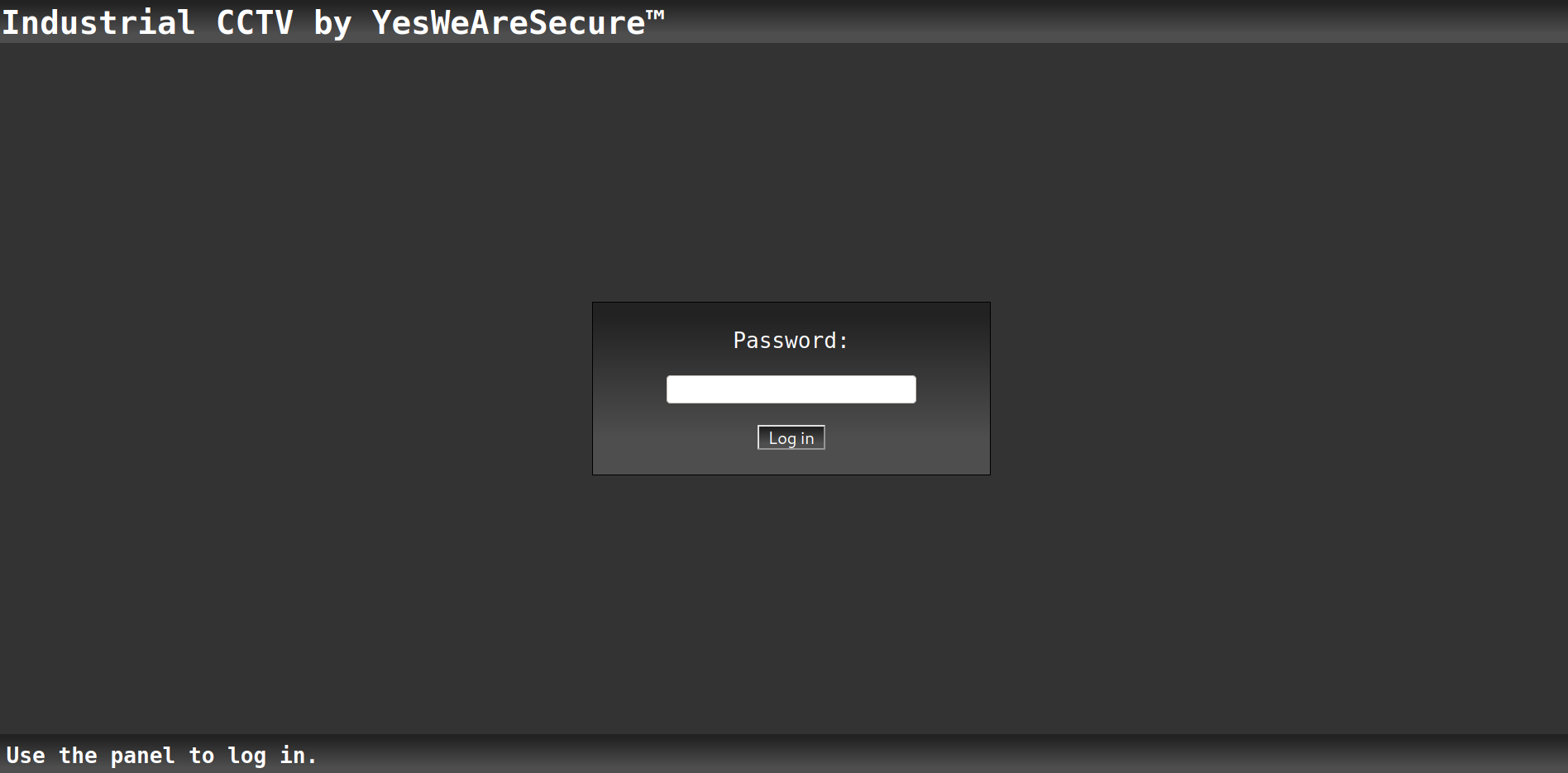
Writeup
This login screen is really straightforward. When a hacker sees a login page, their first instinct is to look for SQL Injection or a brute-force attack (last option).
This page doesn’t seems to request for authentication from a database. Therefore, this website should be static. And since, the challenge name includes (rev) meaning Reverse Engineering we should inspect the source code.
JavaScript from source code:
const checkPassword = () => {
const v = document.getElementById("password").value;
const p = Array.from(v).map(a => 0xCafe + a.charCodeAt(0));
if(p[0] === 52037 &&
p[6] === 52081 &&
p[5] === 52063 &&
p[1] === 52077 &&
p[9] === 52077 &&
p[10] === 52080 &&
p[4] === 52046 &&
p[3] === 52066 &&
p[8] === 52085 &&
p[7] === 52081 &&
p[2] === 52077 &&
p[11] === 52066) {
window.location.replace(v + ".html");
} else {
alert("Wrong password!");
}
}
Diving into code
The script here is simple. A constant v gets input value and is compared to constant p to authenticate the user.
Constant p:
const p = Array.from(v).map(a => 0xCafe + a.charCodeAt(0));
- map() calls a function once for each element in an array.
-
The charCodeAt() method returns the Unicode of the character at a specified index (position) in a string.
- 0xCafe (hexadecimal of 51966) is added to every element in that array and then converted to Unicode or ASCII to compare user input.
My theory
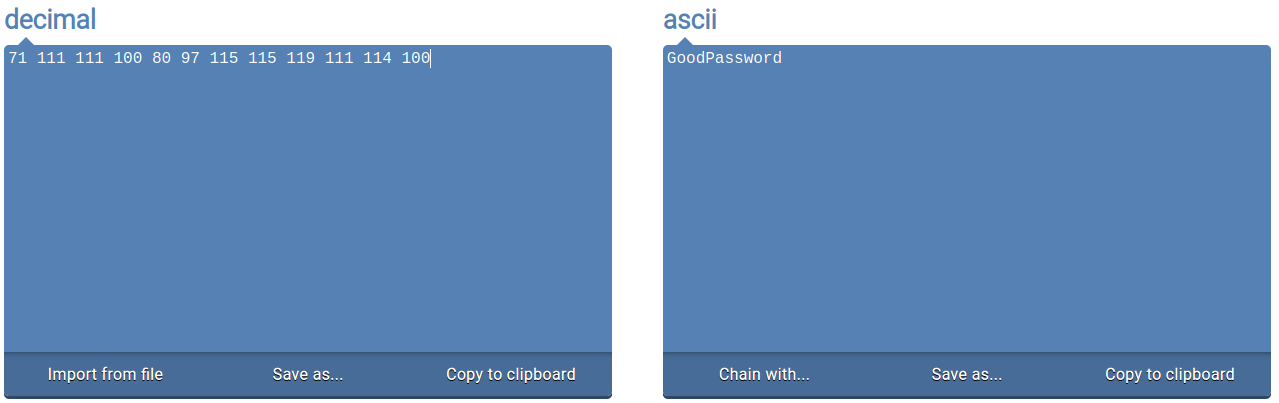
My theory is that you subtract 51966 (the decimal value of 0xCafe) and then convert the result to ASCII. The password should be that ASCII value.
A simple python script I wrote:
Code:
password = ""
a = [52037,52081,52063,52077,52077,52080,52046,52066,52085,52081,52077,52066]
for i in range(len(a)):
a[i] = a[i] - 51966 #51966 is decimal value of 0xCafe
password = chr(a[i]) + password
print(password)
Output:
doswdProoasG
If you align each piece of the output with the order in which the array is in the script, you’ll obtain GoodPassword as the password. Which is, in fact, the login page’s password.
Thank you for taking the time to read this article. I hope you gained some new knowledge. Don’t forget to take a look at my other articles.
